As improving TCP is a long-term goal for Google, QUIC aims to be nearly equivalent to an independent TCP connection, but with much reduced latency (goal: 0-RTT connectivity overhead) and better SPDY-like stream-multiplexing support; if QUIC features prove effective, those features could migrate into a later version of TCP and TLS (which have a notably longer deployment cycle). With QUIC, Google aims to combine some of the best features of UDP and TCP with modern security tools.
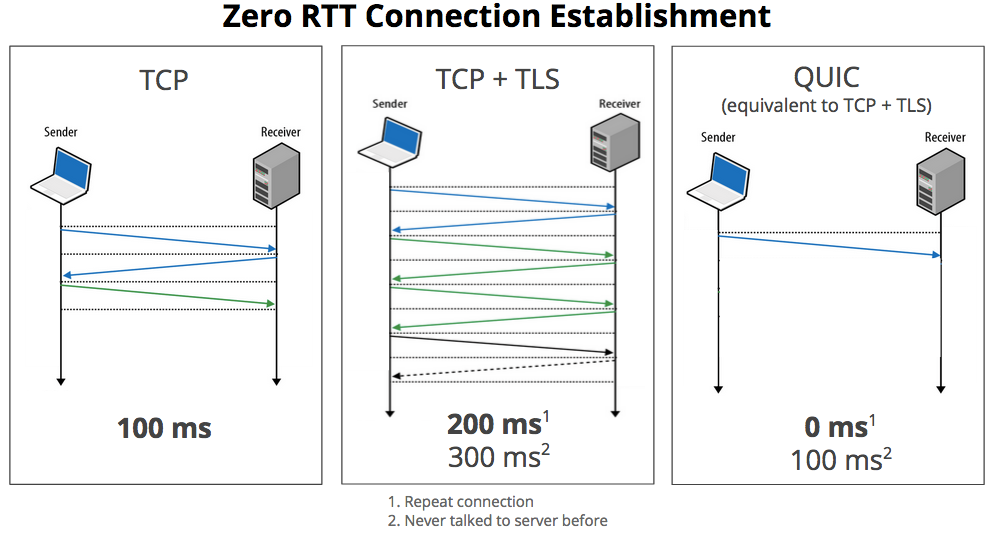
On a typical secure TCP connection, it typically takes two or three round-trips before the browser can actually start receiving data. Using QUIC, a browser can immediately start talking to a server it has talked to before. QUIC also introduces a couple of new features like congestion control and automatic re-transmission, making it more reliable that pure UDP.
With SPDY, which later became the basis for the HTTP/2 standard, Google already developed another alternative protocol that had many of the same goals as QUIC, but HTTP/2 still runs over TCP and still runs into some of the same latency cost.
It’s reasonable to ask why Google doesn’t just work on improving TCP instead then. The problem here, the company points out, is that TCP support is often built directly into operating system kernels — and that’s not something Google has any control over. “QUIC allows us to test and experiment with new ideas, and to get results sooner,” the team writes in explaining its decision. “We are hopeful that QUIC features will migrate into TCP and TLS if they prove effective.”
If Google designed a whole new protocol, then all of the machines that make up the backbone of the Internet would also have to understand it — but they already understand UDP.
QUIC (Quick UDP Internet Connections) is an experimental transport layer network protocol developed by Google. Starting from 2015, some sites (For example Google and YouTube) offer connection via QUIC protocol. Google Chrome support it in latest version by default. QUIC uses UDP port 80 and port 443 and often permits clients to bypass transparent proxies, in which UTM feature such as web filtering may not work properly on Google Chrome only, but works perfectly on other browsers such as Internet Explorer or Mozilla Firefox.
There are three ways to block/disable QUIC:
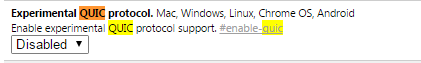
Method 1: Disable Experimental QUIC protocol on Google Chrome browser. – This can be done by opening Google Chrome, in the URL type “chrome://flags”. Look for Experimental QUIC protocol and disable it.
Method 2: Block QUIC using Application Control – Go to Application Control profile, look for Application signature name “QUIC” and select the action “Block”. Apply this Application Control profile into the firewall policy.
![]()
Method 3: Block QUIC using firewall policy – Create a custom firewall service for UDP port 80 and port 443. Configure a firewall policy with the custom service created and set the action to Deny. Make sure this policy on top of all ( inside to outside)